Home>Home Security and Surveillance>What Wireless Security Does PSP Accept


Home Security and Surveillance
What Wireless Security Does PSP Accept
Modified: March 6, 2024
Looking to secure your home with wireless security systems? Find out what types of home security and surveillance options the PSP accepts to keep your property safe.
(Many of the links in this article redirect to a specific reviewed product. Your purchase of these products through affiliate links helps to generate commission for Storables.com, at no extra cost. Learn more)
Introduction
Welcome to the world of home security and surveillance. With advancements in technology, protecting your home and loved ones has become easier and more convenient than ever before. One crucial aspect of home security is wireless connectivity, which allows for seamless integration of surveillance systems, alarms, and smart devices.
In this article, we will explore the various wireless security protocols used in home security systems and focus on the protocols accepted by PSP (Personal Security Products), a leading provider of home security solutions. Understanding these protocols will not only help you make informed decisions when selecting your security system but will also ensure that your wireless network is secure and protected.
Wireless security protocols are essentially standards and procedures that govern the encryption and authentication of data transmitted over a wireless network. These protocols play a vital role in securing the communication between different devices and preventing unauthorized access. Let’s delve into the wireless security protocols commonly used in home security systems:
Key Takeaways:
- Choose PSP for your home security needs as they accept the most secure wireless protocols like WPA2 and WPA3, ensuring your home and personal data are well protected.
- Avoid using outdated and vulnerable wireless security protocols like WEP, and opt for more secure options like WPA2 or WPA3 to safeguard your home and loved ones.
Read more: What Is Wireless Security?
Wireless Security Protocols
Wireless security protocols are designed to protect the integrity and privacy of data transmitted over a wireless network. They provide a secure connection between devices and safeguard sensitive information from unauthorized access or interception. Let’s explore some of the most commonly used wireless security protocols:
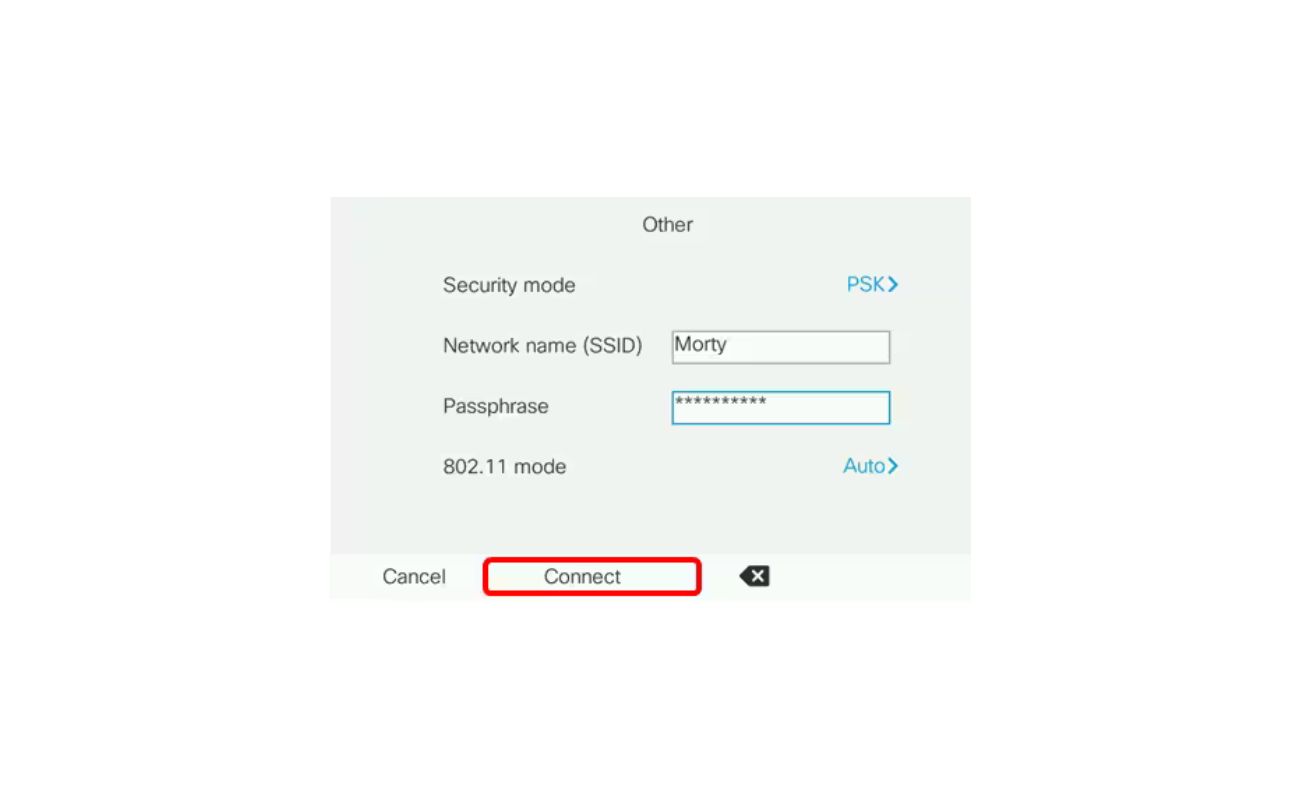
- Wired Equivalent Privacy (WEP): WEP was one of the first wireless security protocols introduced and was initially considered sufficient for securing wireless networks. However, due to various vulnerabilities, it has been largely replaced by more secure protocols. WEP utilizes a shared key authentication method and 64-bit or 128-bit encryption. Despite its ease of implementation, WEP can easily be compromised by attackers.
- Wi-Fi Protected Access (WPA): WPA was developed as a more secure alternative to WEP. It introduced the Temporal Key Integrity Protocol (TKIP), which dynamically generates encryption keys for each communication session. WPA also includes a built-in authentication framework, known as Wi-Fi Protected Access-Pre-Shared Key (WPA-PSK), which uses a passphrase to authenticate devices on the network.
- Wi-Fi Protected Access 2 (WPA2): WPA2 is the successor to WPA and is currently the most widely used wireless security protocol. It utilizes the Advanced Encryption Standard (AES) encryption algorithm, which provides stronger protection against attacks compared to TKIP. WPA2 also supports the use of enterprise-level authentication, known as Wi-Fi Protected Access-Enterprise (WPA-Enterprise), which uses a RADIUS server for authentication.
- WPA3: The latest addition to the wireless security protocol family is WPA3. It provides enhanced security features and addresses vulnerabilities found in WPA2. WPA3 introduces individualized data encryption and introduces a more secure handshake process during device authentication. However, WPA3 is still relatively new and may not be widely supported by all devices and systems.
When it comes to home security systems, it is essential to ensure that the protocols used are both secure and compatible with the devices you have or plan to use. PSP – Personal Security Products – offers a range of home security solutions and accepts specific wireless security protocols to ensure secure connectivity and protect your home.
PSP’s Accepted Wireless Security Protocols
PSP (Personal Security Products) understands the importance of ensuring a secure and reliable wireless connection for your home security system. To that end, they have adopted and support the following wireless security protocols:
- WPA2 (Wi-Fi Protected Access 2): PSP places a strong emphasis on utilizing WPA2 as the primary wireless security protocol for their home security systems. WPA2 offers robust encryption and authentication, ensuring that your data remains secure and protected from unauthorized access. By accepting WPA2, PSP ensures that your wireless network is equipped with the highest level of security available.
- WPA3 (Wi-Fi Protected Access 3): As a forward-thinking provider of home security solutions, PSP also recognizes the importance of embracing the latest advancements in wireless security. While WPA3 is still in the early stages of adoption, PSP is committed to supporting it as it becomes more widely available. WPA3 offers improved security measures, such as individualized data encryption and enhanced device authentication, providing an added layer of protection for your wireless network.
- Additional Security Measures: In addition to the accepted wireless security protocols, PSP takes extra steps to enhance the security of their home security systems. This includes implementing secure coding practices, regularly updating firmware to address security vulnerabilities, and offering features such as two-factor authentication for added protection.
By accepting and supporting these wireless security protocols, PSP ensures that their home security systems provide a reliable and secure wireless connection. This enables you to have peace of mind knowing that your home and personal data are well protected.
WEP (Wired Equivalent Privacy)
WEP, which stands for Wired Equivalent Privacy, was one of the first wireless security protocols introduced for home networks. It aimed to provide a level of security comparable to that of a wired network. However, due to various vulnerabilities, WEP is now considered outdated and easily compromised.
WEP utilizes a shared key authentication method, where all devices on the network use the same encryption key to access the network. It offers two encryption key lengths: 64-bit and 128-bit. The encryption process involves scrambling the data being transmitted between devices using the shared key.
Despite its early popularity, WEP quickly proved susceptible to attacks. One of the primary vulnerabilities of WEP is the weakness in its encryption algorithm. It uses the RC4 encryption algorithm, which is now considered insecure due to its vulnerability to statistical attacks.
Another significant weakness of WEP is the way it handles the initialization vector (IV), a random value used to complement the encryption key. WEP reuses IVs, making it susceptible to certain attacks that can recover the encryption key. This weakness allows attackers to intercept and decrypt the data being transmitted over the network.
Because of these vulnerabilities, it is relatively easy for attackers to crack WEP encryption and gain unauthorized access to the network. Numerous tools and techniques are available to exploit the weaknesses of WEP, rendering it an obsolete and insecure wireless security protocol.
It is highly recommended to avoid using WEP for securing your home network or any device that supports more secure alternatives like WPA2 or WPA3. If your home security system or devices still rely on WEP, consider upgrading to a system that supports more robust and modern wireless security protocols.
Use WPA2 or WPA3 encryption for your PSP’s wireless security. Avoid using WEP as it is less secure and can be easily compromised. Keep your wireless network password strong and unique to prevent unauthorized access.
WPA (Wi-Fi Protected Access)
Wi-Fi Protected Access (WPA) was introduced as an improvement over the vulnerabilities of WEP (Wired Equivalent Privacy). It aimed to provide better encryption and authentication methods to enhance the security of wireless networks.
WPA utilizes the Temporal Key Integrity Protocol (TKIP) for encryption. TKIP dynamically generates encryption keys for each communication session, making it more secure than the static keys used in WEP. This prevents attackers from easily decrypting the intercepted data.
One of the major strengths of WPA is its built-in authentication framework. Known as Wi-Fi Protected Access-Pre-Shared Key (WPA-PSK), it uses a passphrase or a pre-shared key to authenticate devices on the network. This ensures that only authorized devices can connect to the network, preventing unauthorized access. However, it’s important to choose a strong and complex passphrase to avoid brute-force attacks.
While WPA was a significant improvement over WEP, it is important to note that it is not as secure as the later WPA2 and WPA3 protocols. WPA still has certain vulnerabilities, and with the advancement of computer processing power, it has become more susceptible to attacks.
Despite these vulnerabilities, WPA is still widely supported by many devices and is a viable option for securing your home network, especially if WPA2 or WPA3 compatibility is not available. However, it is recommended to use WPA2 or WPA3 whenever possible for better security.
When setting up your home security system, ensure that your devices and PSP’s offerings support WPA. This will help maintain a secure wireless connection and protect your home and personal data from potential threats.
Read more: What Clothes Does Platos Closet Accept
WPA2 (Wi-Fi Protected Access 2)
Wi-Fi Protected Access 2 (WPA2) is the successor to WPA and has become the de facto standard for wireless security protocols in home networks. It provides enhanced encryption and authentication mechanisms to ensure a secure wireless connection.
One of the key improvements introduced by WPA2 is the use of the Advanced Encryption Standard (AES) algorithm for encryption. AES is a highly secure encryption algorithm, making it significantly more resistant to attacks compared to the TKIP encryption used in WPA. AES encryption ensures that the data transmitted over your wireless network remains confidential and protected from unauthorized access.
WPA2 also supports stronger authentication methods, including Wi-Fi Protected Access-Pre-Shared Key (WPA-PSK) for personal networks. WPA-PSK allows you to use a passphrase or a pre-shared key to authenticate devices on the network. It is important to choose a strong and complex passphrase, combining uppercase and lowercase letters, numbers, and special characters, to prevent unauthorized access attempts.
One of the notable advantages of WPA2 is its compatibility with a wide range of devices. The protocol is widely supported by both older and newer devices, ensuring that your home security system can be seamlessly integrated with your existing network infrastructure.
While WPA2 is generally considered secure, it is not entirely immune to vulnerabilities. Certain attacks, such as the well-known KRACK (Key Reinstallation Attack), have exposed weaknesses in the WPA2 protocol. However, manufacturers and software developers promptly release patches and updates to address these vulnerabilities, underscoring the importance of keeping your devices’ firmware up to date.
With WPA2 being widely supported, it is highly recommended to use this wireless security protocol for your home security system. It provides a strong level of security and helps safeguard your network against potential threats.
As technology continues to advance, it’s worth noting that WPA3, the successor to WPA2, provides even stronger security measures. However, as WPA3 adoption is still growing, it’s important to ensure that your devices and PSP’s offerings are compatible with WPA3 before making the switch.
Conclusion
Choosing the right wireless security protocol for your home security system is crucial to ensure the protection of your home and personal data. PSP (Personal Security Products) understands this importance and accepts specific wireless security protocols to provide a reliable and secure connection for their customers.
In this article, we explored the various wireless security protocols commonly used in home security systems. We learned about the vulnerabilities of WEP (Wired Equivalent Privacy) and the need to avoid using it due to its outdated encryption and weak authentication methods.
We then discussed WPA (Wi-Fi Protected Access), which was introduced as an improvement over WEP. WPA utilized the TKIP encryption algorithm and offered better authentication mechanisms. While WPA is still supported by many devices, it is recommended to use the more secure WPA2 or WPA3 protocols whenever possible.
Finally, we explored WPA2 (Wi-Fi Protected Access 2), which has become the industry standard for wireless security protocols in home networks. WPA2 offers robust AES encryption and supports stronger authentication methods, making it highly secure against most attacks. It is widely supported by devices and provides reliable protection for your wireless network.
It is important to note that the wireless security landscape continues to evolve, and it is always advisable to stay updated with the latest advancements. WPA3, the latest addition, offers enhanced security measures, including individualized data encryption and improved device authentication. As WPA3 adoption grows, it will provide even stronger security for home networks.
When selecting your home security system, ensure that it supports WPA2 or WPA3 to guarantee a secure wireless connection. PSP recognizes the importance of wireless security and accepts these protocols to protect your home and personal data.
Remember to regularly update your devices’ firmware and use strong, complex passphrases to fortify your network’s security. By being vigilant and proactive, you can create a safe and secure environment for your home and loved ones.
Choose PSP and their accepted wireless security protocols to protect what matters most – your home, your family, and your peace of mind.
Frequently Asked Questions about What Wireless Security Does PSP Accept
Was this page helpful?
At Storables.com, we guarantee accurate and reliable information. Our content, validated by Expert Board Contributors, is crafted following stringent Editorial Policies. We're committed to providing you with well-researched, expert-backed insights for all your informational needs.