Home>Home Security and Surveillance>What Wireless Security Options To Use


Home Security and Surveillance
What Wireless Security Options To Use
Modified: March 6, 2024
Learn about the best wireless security options for home security and surveillance. Discover the latest technologies to ensure the safety and protection of your property.
(Many of the links in this article redirect to a specific reviewed product. Your purchase of these products through affiliate links helps to generate commission for Storables.com, at no extra cost. Learn more)
Introduction
Welcome to the world of wireless security! In today’s digital age, protecting our homes and our loved ones has become more important than ever. With the rapid advancement of technology, home security systems have evolved to include wireless options that provide convenience, flexibility, and peace of mind.
Wireless security systems offer a range of benefits, from easy installation to remote access and control. However, with the rise in cyber threats and hacking attempts, it’s crucial to understand the basics of wireless security to ensure maximum protection of our homes and personal information.
In this article, we will explore different wireless security options and discuss best practices to safeguard your home and loved ones. So, let’s dive into the world of wireless security and discover the key steps to secure your home network.
But before we jump into the specifics, let’s start with the foundation: password protection.
Key Takeaways:
- Secure your home network by using strong passwords, MAC address filtering, and encryption methods like WPA2 to protect against unauthorized access and safeguard personal information.
- Enhance wireless security with VPNs and network segmentation to create secure zones, limit security breaches, and protect sensitive data within your home network.
Read more: What Wireless Security Should You Use
Wireless Security Basics
When it comes to wireless security, it’s essential to understand the fundamental principles that form the basis of a secure system. These principles include password protection, MAC address filtering, encryption methods, and network segmentation.
First and foremost, setting a strong password is crucial for securing your wireless network. A weak password can leave your network vulnerable to unauthorized access. Be sure to choose a password that is unique, complex, and not easily guessable. Avoid using common words or personal information in your password. Instead, opt for a combination of uppercase and lowercase letters, numbers, and special characters.
In addition to password protection, you can enhance wireless security by implementing MAC address filtering. MAC address is a unique identifier assigned to each network device. By enabling MAC address filtering, you can define a list of authorized devices that are allowed to connect to your network. This ensures that only trusted devices can access your network, providing an extra layer of protection against unauthorized access.
Now let’s discuss the importance of encryption methods in wireless security. Encryption is the process of encoding data to prevent it from being accessed by unauthorized users. It ensures that information transmitted over your wireless network is secure and cannot be intercepted or deciphered by potential attackers.
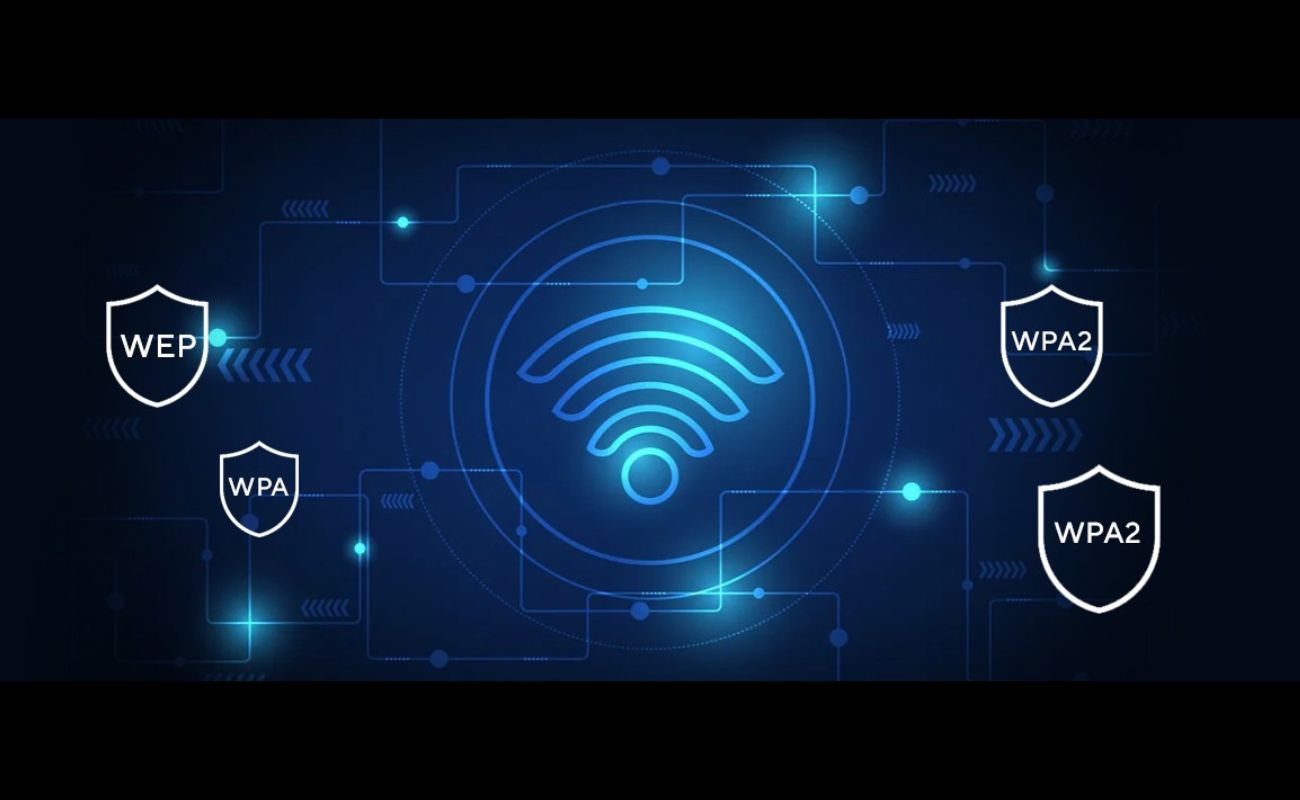
One of the widely used encryption methods is Wi-Fi Protected Access (WPA). It provides stronger security than the previous Wired Equivalent Privacy (WEP) protocol. WPA utilizes dynamic encryption keys, making it more difficult for hackers to crack. It’s important to note that WPA requires a strong passphrase for authentication, so choose a complex passphrase to prevent unauthorized access.
Another encryption method is Wi-Fi Protected Access 2 (WPA2). It is currently the most secure encryption standard available for wireless networks. WPA2 uses a stronger encryption algorithm called Advanced Encryption Standard (AES). AES provides a higher level of security, offering protection against various security attacks.
Lastly, considering network segmentation can further enhance your wireless security. Network segmentation involves dividing your network into different subnetworks or VLANs (Virtual Local Area Networks). By separating devices into different segments based on their roles and access levels, you can restrict unauthorized access and contain potential security breaches within specific areas of your network.
Understanding these wireless security basics is essential for creating a secure home network. By implementing password protection, MAC address filtering, encryption methods, and network segmentation, you can significantly reduce the chances of unauthorized access and protect your home and personal information.
Password Protection
Password protection is the first line of defense when it comes to securing your wireless network. A strong and unique password can greatly reduce the risk of unauthorized access and potential security breaches.
Here are some best practices to follow when setting up a secure password for your wireless network:
- Choose a unique password: Avoid using common or predictable passwords, such as “password” or “12345678”. Hackers often use automated programs that can quickly guess these simple passwords. Instead, create a unique password that combines uppercase and lowercase letters, numbers, and special characters.
- Length matters: The longer the password, the more secure it is. Aim for a minimum of 8-12 characters, but consider using even longer passwords for added security.
- Avoid personal information: Avoid using personal information, such as your name, date of birth, or address, in your password. This information can be easily guessed or obtained by someone who knows you.
- Use a passphrase: Consider using a passphrase instead of a single-word password. Passphrases are longer phrases or sentences that are easier for you to remember but harder for hackers to crack. For example, “MyFavoriteSongIs1984!” or “Ilovetotravelin2022$”.
- Regularly change your password: It’s a good practice to change your password periodically, ideally every 3-6 months. Regularly changing your password can help prevent unauthorized access and keep your network secure.
- Don’t share your password: Avoid sharing your Wi-Fi password with people you don’t trust or who don’t need access to your network. The more people who know the password, the greater the risk of unauthorized access.
- Securely store your password: When you do write down or store your Wi-Fi password, make sure it is stored in a secure place. Avoid keeping it in plain sight or on easily accessible devices, such as a sticky note on your desk or a document on your computer desktop.
By following these password protection best practices, you can significantly improve the security of your wireless network. Remember, a strong and unique password is the first step towards safeguarding your home and personal information from potential cyber threats.
MAC Address Filtering
An additional layer of protection for your wireless network is MAC address filtering. MAC address filtering allows you to specify which devices are allowed to connect to your network based on their unique MAC addresses.
Every network interface card (NIC) has a unique MAC address assigned to it. By enabling MAC address filtering on your wireless router, you can create a whitelist of approved MAC addresses. Only devices with MAC addresses on this list will be granted access to your network, while all other devices will be denied.
Here’s how you can implement MAC address filtering to enhance your wireless security:
- Access your router settings: To enable MAC address filtering, you’ll need to access your router’s configuration settings. Open a web browser and enter your router’s IP address in the address bar. You may need to provide your router’s username and password to log in.
- Locate the MAC address filtering settings: Once logged into your router’s configuration page, navigate to the wireless security or wireless settings section. Look for an option related to MAC address filtering or MAC access control.
- Enable MAC address filtering: Select the option to enable MAC address filtering. This will activate the feature and allow you to configure the whitelist of MAC addresses.
- Add MAC addresses to the whitelist: Find the option to add MAC addresses to the whitelist. You can typically do this by entering the MAC address manually or selecting devices that are currently connected to your network.
- Save and apply the changes: After adding the MAC addresses to the whitelist, save the changes and apply them to your router’s settings. This will activate MAC address filtering, and only approved devices will be able to connect to your network.
While MAC address filtering provides an extra layer of security, it’s important to note that MAC addresses can be spoofed or cloned by sophisticated attackers. However, this added measure can still deter casual unauthorized users and prevent easy access to your network.
It’s essential to regularly review and update the MAC address whitelist as needed. When purchasing new devices, you’ll need to add their MAC addresses to the list to grant them access to your network. Similarly, if you remove a device or no longer want it to have access, you should remove its MAC address from the whitelist.
By implementing MAC address filtering alongside other security measures like password protection and encryption, you can further enhance the security of your wireless network and protect your home and personal information from unauthorized access.
Encryption Methods
Encryption plays a crucial role in securing your wireless network by protecting the confidentiality and integrity of the data transmitted over the airwaves. Encryption involves encoding the data into an unreadable format that can only be deciphered by authorized devices with the correct decryption key.
There are various encryption methods available for wireless networks. Let’s explore some commonly used encryption methods and their strengths:
- Wired Equivalent Privacy (WEP): WEP was the first encryption standard introduced for wireless networks. However, it has significant security vulnerabilities and is no longer considered secure. WEP uses a shared key that is easily crackable, making it susceptible to hacking.
- Wi-Fi Protected Access (WPA): WPA was developed to address the security weaknesses found in WEP. It uses a stronger encryption algorithm called Temporal Key Integrity Protocol (TKIP). WPA dynamically changes encryption keys for every packet transmitted, making it more secure than WEP. However, WPA is still vulnerable to certain attacks.
- Wi-Fi Protected Access 2 (WPA2): Currently, WPA2 is the most commonly used and recommended encryption protocol for wireless networks. It uses the more secure Advanced Encryption Standard (AES) algorithm. AES is a symmetric encryption algorithm that provides stronger security and is less susceptible to attacks. WPA2 is considered highly secure when paired with a strong password.
- Wi-Fi Protected Access 3 (WPA3): WPA3 is the latest encryption standard for wireless networks, providing even stronger security than WPA2. It introduces enhanced security features, including improved password protection and forward secrecy. However, as of now, WPA3 adoption is still relatively limited, and many devices may not yet support it.
- VPN (Virtual Private Network): A VPN is an additional layer of security that can be used to encrypt data transmitted over a wireless network. When connected to a VPN, your data is encapsulated and encrypted, making it virtually impossible for anyone to intercept or decipher. VPNs are commonly used when connecting to public Wi-Fi networks to ensure secure transmission of sensitive information.
When it comes to choosing an encryption method for your wireless network, it’s highly recommended to use WPA2 as the minimum standard. WPA3 is the ideal option for maximum security when it becomes more widely supported by devices.
Remember, encryption is only effective if you also have a strong password. The strength of your encryption relies on the strength of your password, so make sure to follow the password protection best practices discussed earlier.
By implementing strong encryption methods and keeping abreast of the latest security standards, you can ensure that your wireless network is protected from potential threats and secure your home and personal information.
Enable WPA2 encryption on your wireless network for strong security. Use a complex password with a mix of letters, numbers, and symbols to prevent unauthorized access.
Read more: What Is Wireless Security?
Wi-Fi Protected Access (WPA)
Wi-Fi Protected Access (WPA) is an encryption protocol that was developed as an improvement over the weak security of the Wired Equivalent Privacy (WEP) protocol. WPA was introduced to address the vulnerabilities of WEP and provide stronger security for wireless networks.
One of the key features of WPA is the use of Temporal Key Integrity Protocol (TKIP) encryption. TKIP dynamically generates a unique encryption key for each data packet transmitted, making it more resistant to attacks compared to the static encryption key used in WEP. This ensures that even if an attacker manages to crack one encryption key, they cannot gain access to all data packets transmitted over the network.
WPA also introduced the concept of a preshared key (PSK) or a Wi-Fi password. The PSK, also known as the WPA pre-shared key, is a shared secret password that is entered on devices wishing to connect to the wireless network. The PSK is used to authenticate and secure the connection between the device and the wireless access point.
Here are some key points to understand about WPA:
- Backward compatibility: WPA provides backward compatibility with older devices that only support WEP. This allows existing devices to connect to a WPA-enabled network while still benefiting from the improved security offered by WPA.
- Authentication methods: WPA supports two authentication methods: Pre-Shared Key (PSK) and 802.1X authentication. PSK is the most commonly used method for home networks, where a shared passphrase is used to authenticate devices. 802.1X authentication is typically used in enterprise environments, where a central authentication server is employed.
- Strengths and weaknesses: While WPA provides better security than WEP, it is still vulnerable to certain attacks, such as brute-force dictionary attacks on weak passwords. Therefore, it is essential to use a strong and unique passphrase for your WPA-enabled network.
- WPA2 as an upgrade: WPA2 is an improved version of WPA and provides stronger and more reliable security. It uses the Advanced Encryption Standard (AES) instead of TKIP, making it more resistant to attacks. It is highly recommended to upgrade to WPA2 or use WPA2 as the standard encryption method if your devices support it.
When setting up a wireless network, it is crucial to choose WPA as the minimum encryption option to ensure better security than the outdated WEP. However, for optimal security, it is advisable to use the more advanced WPA2 protocol.
Remember to create a strong passphrase for your WPA-enabled network, avoiding common words or personal information. Regularly updating the Wi-Fi password and keeping an eye on security updates and patches for your devices and router are also important to maintain a secure wireless network.
By implementing WPA and following security best practices, you can significantly enhance the security of your wireless network and protect your home and personal information from potential threats.
Wi-Fi Protected Access 2 (WPA2)
Wi-Fi Protected Access 2 (WPA2) is currently the most secure encryption standard for wireless networks. It is an improvement over its predecessor, WPA, and provides stronger security measures to protect your network from potential threats.
Here are some key aspects to understand about WPA2:
- Advanced Encryption Standard (AES): WPA2 uses the Advanced Encryption Standard (AES) algorithm, which is considered highly secure and much stronger than the TKIP encryption used in WPA. AES uses a 128-bit block size and key length, offering robust protection against brute-force attacks.
- CCMP encryption protocol: WPA2 employs the Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP) as its encryption protocol. CCMP ensures the integrity and confidentiality of data transmitted over the wireless network, providing robust security against unauthorized access and data interception.
- PSK and 802.1X authentication: WPA2 supports both Pre-Shared Key (PSK) authentication and 802.1X authentication methods. PSK is commonly used in home networks, where a shared passphrase or Wi-Fi password is used to authenticate devices. 802.1X authentication is more commonly used in enterprise environments, where a centralized authentication server is utilized.
- Stronger security measures: WPA2 provides several security enhancements over WPA, including improved encryption, stronger key management, and resistance to various security attacks. Its implementation of AES encryption and CCMP protocol make it highly secure for wireless networks.
- Recommended security standard: Given its robust encryption and security measures, WPA2 is the recommended security standard for wireless networks. It offers the highest level of protection for your network and helps safeguard your home and personal information from potential threats.
It is important to note that while WPA2 is highly secure, its effectiveness heavily relies on the strength of the Wi-Fi password used. It is crucial to create a strong and unique passphrase, avoiding common words, phrases, and personal information. Additionally, regularly updating the Wi-Fi password and keeping a check on security updates and patches for your devices and router are essential to maintain a secure wireless network.
While WPA3, the successor of WPA2, is available and provides even stronger security features, its adoption is still limited, and many devices may not yet support it. Therefore, WPA2 remains the standard and recommended encryption method for wireless networks.
By implementing WPA2 and following best security practices, you can significantly enhance the security of your wireless network, ensuring the protection of your home and personal information from potential threats.
Virtual Private Networks (VPNs)
Virtual Private Networks (VPNs) provide an additional layer of security for your wireless network by encrypting the data transmitted between your device and the internet. VPNs create a secure and private connection, protecting your online activities from prying eyes and potential cyber threats.
Here’s how VPNs work and why they are beneficial for wireless security:
- Encryption and tunneling: When you connect to a VPN, your data is encrypted and encapsulated within a secure “tunnel” between your device and the VPN server. This encryption ensures that your data remains confidential and protected from unauthorized access.
- Protecting data on public Wi-Fi networks: One of the primary advantages of using a VPN is when connecting to public Wi-Fi networks. Public Wi-Fi networks, such as those found in cafes, airports, or hotels, are often unsecured and vulnerable to interception. By using a VPN, all your internet traffic is encrypted, preventing hackers or eavesdroppers from intercepting your data.
- Bypassing geographical restrictions: VPNs can also be used to bypass geographical restrictions or censorship. By connecting to a VPN server located in a different country, you can appear as if you are browsing from that country, allowing you to access content and services that may be restricted in your location.
- Enhancing privacy: VPNs help protect your online privacy by masking your IP address. By connecting to a VPN server, your IP address is replaced with the IP address of the VPN server. This makes it difficult for websites, advertisers, and other entities to track your online activities and location.
- Securing remote access: VPNs are commonly used to securely access internal networks and resources remotely. This is especially important for businesses, allowing employees to connect to their company’s network from outside locations while ensuring the security and confidentiality of data.
When selecting a VPN provider, consider the following points:
- Reputation and security: Ensure that the VPN provider has a good reputation and a strong commitment to security. Look for providers that use robust encryption algorithms, have a strict no-logs policy, and offer features like kill switches and DNS leak protection.
- Server locations: Choose a VPN provider with servers located in the regions you are interested in accessing or want to secure your connection to. Having a wide range of server locations allows for better flexibility and performance.
- User-friendly interface: Look for VPN providers that offer user-friendly applications and interfaces across different devices and operating systems. This makes it easier to set up and use the VPN on your devices.
- Connection speed: Some VPNs may impact your internet connection speed due to the encryption and routing process. Look for VPN providers that offer fast and stable connections to ensure smooth browsing and streaming experiences.
Using a VPN alongside other wireless security measures such as strong password protection and encryption can significantly enhance the security and privacy of your wireless network. It is especially valuable when connecting to public Wi-Fi networks or when you need to access sensitive information remotely.
Remember to choose a reputable VPN provider and follow best practices for secure VPN usage to maximize the benefits of this powerful security tool.
Network Segmentation
Network segmentation is a technique used to divide a network into smaller subnetworks or VLANs (Virtual Local Area Networks). By doing so, you can create separate zones or segments within your network, each with its own level of access control and security measures. Network segmentation helps improve wireless security by containing potential security breaches and limiting unauthorized access.
Here’s why network segmentation is important for wireless security:
- Improved network performance: Segmenting your network can help improve network performance by reducing network congestion. By separating devices into different segments based on their roles and functions, you can prioritize and allocate network resources more efficiently, ensuring smooth and consistent performance.
- Isolation of sensitive data: With network segmentation, you can isolate sensitive data and devices into separate segments, ensuring that access to this information is tightly controlled. This helps minimize the damage in case of a security breach and prevents unauthorized access to critical data.
- Containment of threats: In the event of a security breach or malware infection, network segmentation helps limit the spread of the threat. By confining the impact to a specific segment, you can prevent the entire network from being compromised, reducing the potential damage and enabling quicker containment and remediation.
- Access control and security zoning: By segmenting your network, you can create different security zones or segments with varying levels of access control. This allows you to apply specific security measures tailored to the requirements of each zone. For example, you can enforce stricter access controls for sensitive areas or critical network resources.
- Compliance and regulatory requirements: In certain industries, such as healthcare or finance, regulatory compliance regarding data privacy and security is mandatory. Network segmentation can help you meet these compliance requirements by ensuring that sensitive data is stored and transmitted within a secure segment of the network.
When implementing network segmentation, consider the following best practices:
- Plan and design: Before implementing network segmentation, carefully plan and design the segments based on your network’s requirements and security needs. Consider factors such as the types of devices, user roles, data sensitivity, and access control policies.
- Implement access controls: Enforce access controls to restrict communication between segments. Use firewalls, routers, or layer 3 switches to control traffic flow between segments, allowing only authorized communication based on predetermined rules.
- Monitor and update: Regularly monitor and update the configurations and access controls for each segment. This ensures that the segmentation remains effective and aligned with your network’s security goals. Stay up-to-date with security patches and firmware updates for the devices handling network segmentation.
- Regular auditing and testing: Perform regular audits and penetration tests to identify any potential vulnerabilities and ensure the efficacy of your network segmentation strategy. This helps identify and rectify any misconfigurations or weaknesses that may have been overlooked.
Network segmentation is a powerful technique to enhance wireless security by isolating critical assets, restricting access to sensitive data, and limiting the impact of security breaches. By implementing network segmentation alongside other security measures such as password protection, encryption, and access controls, you can create a more secure and resilient wireless network.
Conclusion
Congratulations! You have now gained a comprehensive understanding of wireless security options and how to secure your home network effectively. By implementing the following measures and best practices, you can ensure the safety of your home and protect your personal information:
- Password protection: Set a strong and unique password for your Wi-Fi network, ensuring it is not easily guessable and regularly updated.
- MAC address filtering: Enable MAC address filtering to allow only authorized devices to connect to your network.
- Encryption methods: Choose the highest level of encryption available, such as WPA2, to ensure the confidentiality and integrity of your data.
- Virtual Private Networks (VPNs): Use a VPN to add an extra layer of encryption and protect your online activities, especially when connected to public Wi-Fi networks.
- Network segmentation: Divide your network into zones or VLANs to enhance access control and limit potential security breaches.
Remember to regularly update your devices and router firmware to ensure the latest security patches are applied. It’s also important to stay informed about evolving threats and security practices to adapt your strategies accordingly.
By implementing these wireless security measures, you can significantly reduce the risk of unauthorized network access, protect your sensitive information, and maintain a secure home network environment. Additionally, regularly assess and test your security measures to stay ahead of potential vulnerabilities.
Stay proactive and vigilant in your approach to wireless security to safeguard your home and loved ones from cyber threats. With a combination of strong passwords, encryption, secure access controls, and network segmentation, you can enjoy the convenience and benefits of wireless technology while keeping your home network safe and secure.
Frequently Asked Questions about What Wireless Security Options To Use
Was this page helpful?
At Storables.com, we guarantee accurate and reliable information. Our content, validated by Expert Board Contributors, is crafted following stringent Editorial Policies. We're committed to providing you with well-researched, expert-backed insights for all your informational needs.