Home>Home Security and Surveillance>How To Hack Into A Wireless Security Camera


Home Security and Surveillance
How To Hack Into A Wireless Security Camera
Modified: March 6, 2024
Learn how to hack into a wireless security camera for home security and surveillance with our step-by-step guide. Protect your property with these valuable tips and techniques.
(Many of the links in this article redirect to a specific reviewed product. Your purchase of these products through affiliate links helps to generate commission for Storables.com, at no extra cost. Learn more)
Introduction
Welcome to the world of wireless security cameras, where advanced technology meets peace of mind. In today’s fast-paced and interconnected world, protecting our homes and loved ones has become a top priority. While traditional security systems provide a sense of security, they can also be expensive and difficult to install.
Wireless security cameras offer a convenient and effective solution. With their easy setup, portability, and remote access capabilities, these cameras have gained popularity among homeowners and business owners alike.
However, as with any technology, wireless security cameras are not without their vulnerabilities. Hackers and criminals have become increasingly adept at exploiting weaknesses in these devices, using them as a gateway to gain unauthorized access to private spaces and personal information.
This article will explore the world of wireless security cameras, their vulnerabilities, and what steps you can take to protect yourself and your property. Whether you’re a homeowner looking to enhance your home security or a business owner wanting to safeguard your premises, understanding the ins and outs of wireless security cameras is essential.
By the end of this article, you will have a comprehensive understanding of the potential risks associated with wireless security cameras and be equipped with the knowledge needed to secure your devices effectively.
Key Takeaways:
- Protect Your Wireless Security Camera
Change default credentials, update firmware, and secure physical access points to prevent unauthorized access and maintain the privacy of your property and loved ones. - Be Ethical and Legal
Hacking into someone else’s wireless security camera is illegal and unethical. Prioritize the security of your own devices and respect the privacy of others.
Understanding Wireless Security Cameras
When it comes to choosing a wireless security camera, it’s essential to know the different types available, how they work, and the common security measures they offer. Let’s delve into each of these aspects to gain a better understanding.
Types of Wireless Security Cameras
There are several types of wireless security cameras available on the market, each with its own unique features and capabilities. Let’s take a closer look at some of the most popular ones:
- Indoor Cameras: These cameras are designed to be used inside the premises and are ideal for monitoring specific areas like entryways, halls, or rooms.
- Outdoor Cameras: Specifically designed to withstand harsh weather conditions, outdoor cameras are perfect for monitoring the exterior of your property, including entrances, driveways, and yards.
- Pan-Tilt-Zoom (PTZ) Cameras: PTZ cameras can be remotely controlled to pan, tilt, and zoom, providing a wide range of coverage and the ability to focus on specific areas of interest.
- Battery-Powered Cameras: As the name suggests, these cameras run on battery power, making them highly portable and suitable for temporary surveillance needs. They can be easily recharged or replaced.
- Hidden Cameras: Sometimes referred to as covert or spy cameras, hidden cameras are designed to be discreetly placed in objects like clocks, smoke detectors, or even stuffed animals.
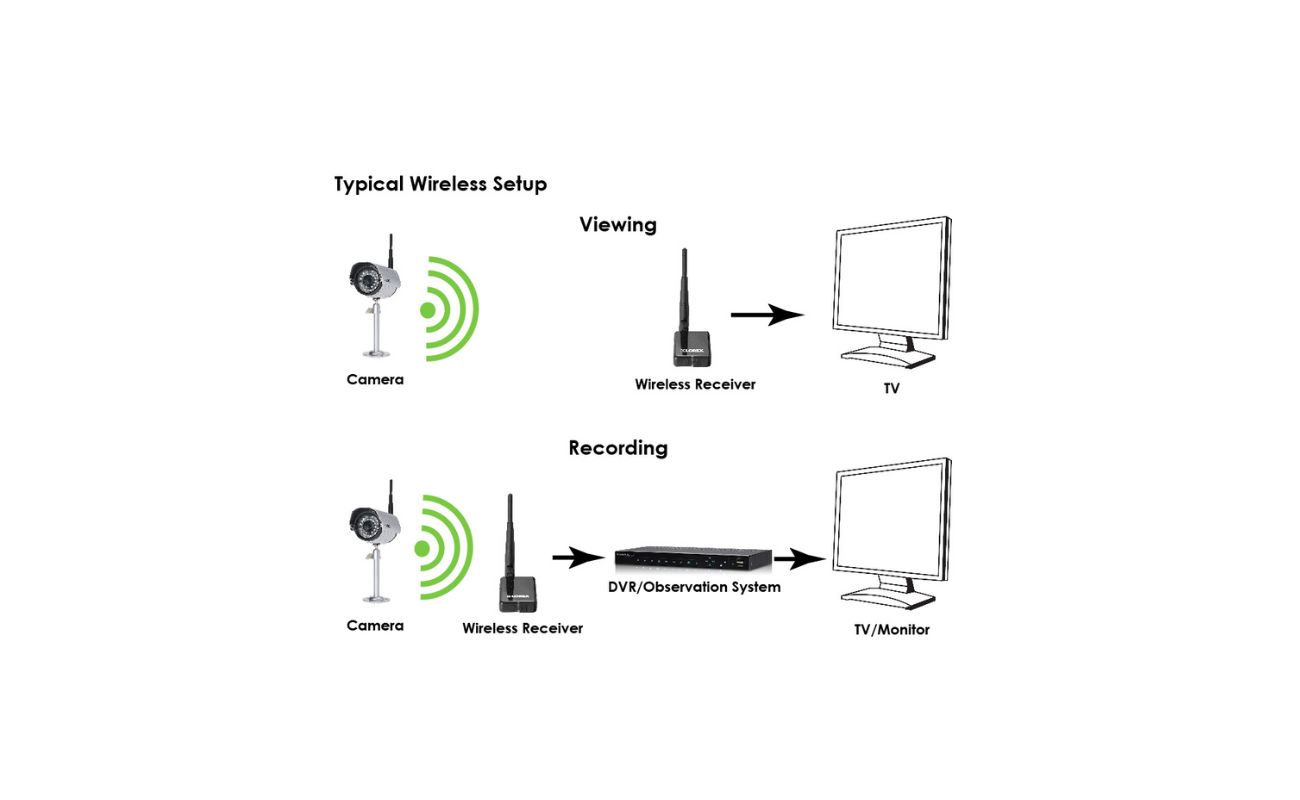
How Wireless Security Cameras Work
Wireless security cameras operate using Wi-Fi or Bluetooth technology to transmit video and audio signals to a receiver or a cloud-based storage system. Here’s a simplified overview of the process:
- The camera captures video footage and audio, if applicable.
- The captured data is encoded and compressed for efficient transmission.
- The camera wirelessly transmits the encoded data to a receiver, which may be connected to a monitoring device or stored in the cloud.
- The receiver decodes and decompresses the data, allowing users to view the live footage or access recorded videos.
Common Security Measures
Wireless security cameras come equipped with various security measures to protect against unauthorized access and ensure data privacy. Here are some common security features to look out for:
- Encryption: Most wireless security cameras employ encryption protocols, such as WPA2, to secure the transmission of data. This ensures that the footage cannot be intercepted or tampered with by unauthorized individuals.
- Login Credentials: User authentication is a crucial security measure. Cameras typically require a username and password to access the live feed or settings, preventing unauthorized access.
- Remote Access Security: Many cameras offer remote access capabilities, allowing users to view the footage from anywhere using a smartphone, tablet, or computer. It’s important to choose cameras that employ secure remote access protocols to prevent unauthorized access from external networks.
- Two-Factor Authentication: Some advanced wireless security cameras offer two-factor authentication as an additional layer of security. This requires users to provide a second form of identification, such as a unique code sent to their mobile device, before gaining access to the camera’s settings or live feed.
- Firmware Updates: Regular firmware updates ensure that your camera is equipped with the latest security patches, addressing any vulnerabilities that may have been discovered.
By understanding the different types of wireless security cameras available, how they work, and the security measures they offer, you can make an informed decision on the best camera for your specific needs. In the next section, we will explore the vulnerabilities that hackers may exploit to gain unauthorized access to your wireless security cameras.
Read more: How To Hack Into Security Cameras
Identifying Vulnerabilities in Wireless Security Cameras
While wireless security cameras provide convenience and enhanced monitoring capabilities, they are not immune to vulnerabilities that can be exploited by hackers. It’s crucial to understand these vulnerabilities to better protect your devices and maintain the security of your property. Let’s explore some common vulnerabilities to be aware of:
Default Credentials
One of the most common vulnerabilities found in wireless security cameras is the use of default credentials. Manufacturers often assign default usernames and passwords to simplify the setup process. Unfortunately, many users overlook the importance of changing these default credentials, making it easy for hackers to gain unauthorized access. It’s essential to change the default credentials as soon as you set up the camera to prevent any potential breaches.
Weak Encryption
The encryption used to secure the transmission of data plays a vital role in protecting the privacy of your surveillance footage. However, some wireless security cameras may use weak encryption protocols or outdated algorithms, making them more susceptible to hacking attempts. It is crucial to choose cameras that utilize strong encryption, such as WPA2, to ensure the security of your data. Additionally, regularly updating your camera’s firmware can help address any encryption vulnerabilities that may arise.
Lack of Firmware Updates
Firmware updates are essential for maintaining the security and functionality of your wireless security cameras. These updates often include bug fixes and security patches that address discovered vulnerabilities. However, some users fail to keep their cameras’ firmware up to date, unknowingly leaving their devices exposed to potential threats. Ensuring that you regularly check for and install firmware updates is vital in safeguarding your cameras against potential attacks.
Read more: How To Hack Into A Wired Security Camera
Physical Access Points
While wireless security cameras are designed to be remotely accessed, physical access points like power outlets, ethernet ports, or reset buttons can be potential vulnerabilities if not adequately secured. Hackers with physical access to the camera can gain control over the device, manipulate settings, or even tamper with the footage directly. It’s important to locate your cameras in secure areas and make efforts to physically protect them from unauthorized access.
Identifying these vulnerabilities is the first step towards mitigating potential risks and strengthening the security of your wireless security cameras. In the next section, we will delve into the preparations required to hack into a wireless security camera, providing insight into how attackers may exploit these vulnerabilities.
Preparing for the Hack
Before attempting to hack into a wireless security camera, it’s crucial to gather the necessary tools, conduct thorough research on the target camera, and identify potential vulnerabilities. Proper preparation ensures a higher chance of success and helps you understand the security risks involved. Let’s explore the key aspects of preparing for a hack:
Gathering Necessary Tools
Hacking into a wireless security camera requires specific tools to exploit vulnerabilities and gain unauthorized access. Some common tools used by hackers include:
- Port Scanners: These tools scan the target camera’s IP address for open ports, helping identify potential entry points for exploitation.
- Password Crackers: Password cracking tools are used to uncover weak or default passwords, allowing hackers to gain access to the device.
- Network Sniffers: Network sniffers help analyze network traffic and capture data packets, potentially revealing sensitive information or vulnerabilities.
- Firmware Exploitation Tools: Exploitation tools are used to identify vulnerabilities in the camera’s firmware and exploit them to gain control.
- Wireless Signal Analyzers: These tools help identify wireless signals and analyze their encryption protocols, assisting in finding weaknesses in the camera’s wireless transmission.
It’s important to note that using these tools for unauthorized access is illegal and unethical. This section is intended for educational purposes only, highlighting the potential risks and vulnerabilities of wireless security cameras.
Researching Target Camera
Before attempting to hack into a specific wireless security camera, it’s essential to research and gather information about the device. This includes identifying the model, manufacturer, and firmware version. By understanding the camera’s specifications, you can narrow down potential vulnerabilities and techniques that can be employed during the hack.
Additionally, research can help you find security advisories or vulnerability reports related to the target camera. This information can provide valuable insights into known weaknesses that you can leverage during the hack.
Read more: How To Hack Home Security Cameras
Finding Vulnerabilities
Once you have gathered information about the target camera, the next step is to find vulnerabilities that can be exploited. This can be done through a variety of methods:
- Online Research: Conducting online searches using specific keywords related to the camera, firmware version, and known vulnerabilities can help uncover any reported weaknesses.
- Security Forums and Communities: Engaging with security forums and communities can provide valuable information from other researchers or individuals who have encountered vulnerabilities in the target camera.
- Reverse Engineering: Reverse engineering involves analyzing the camera’s firmware to identify potential vulnerabilities that can be exploited. This method requires technical expertise and can be time-consuming.
- Penetration Testing: Conducting a penetration test on the camera’s network can help identify potential weaknesses or entry points for exploitation.
By investing time in thorough preparation, including gathering the necessary tools, researching the target camera, and finding potential vulnerabilities, you can increase your understanding of the target device’s security and potential exploitable weaknesses. However, it’s important to remember that hacking into someone else’s wireless security camera is illegal and unethical. The information provided in this section is solely for educational purposes and to create awareness about the vulnerabilities that exist in these devices.
Hacking into the Wireless Security Camera
Once you’ve prepared and identified the vulnerabilities, it’s important to understand the methods hackers may use to gain unauthorized access to a wireless security camera. This section will explore some common techniques that hackers employ:
Exploiting Default Credentials
The use of default credentials is a prevalent security weakness in many wireless security cameras. Hackers can exploit this vulnerability by simply trying common default usernames and passwords provided by the manufacturer. If the camera owner has not changed these default credentials, the hacker can easily gain access and control over the device. It is essential to change the default credentials immediately after setting up a camera to mitigate this risk.
Cracking Weak Encryption
If a wireless security camera uses weak or outdated encryption protocols, hackers may attempt to crack the encryption to gain unauthorized access to the camera’s footage and settings. By analyzing the wireless signals transmitted by the camera, hackers can try to identify weaknesses in the encryption algorithm and exploit them to gain access. It is crucial to choose a camera that uses strong encryption methods, regularly update the firmware, and ensure the security of your wireless network to prevent this type of attack.
Read more: What Security Cameras Cannot Be Hacked
Performing a Brute Force Attack
A brute force attack involves systematically attempting all possible combinations of usernames and passwords until the correct credentials are found. If a wireless security camera has weak or easily guessable credentials, hackers can employ brute force techniques to gain access. This method can be time-consuming but can be effective if the camera owner has chosen a weak password. To protect against brute force attacks, it is essential to choose strong, unique passwords and enable account lockouts after a certain number of failed login attempts.
Accessing Through Physical Access Points
While wireless security cameras are designed to be remotely accessed, physical access points such as power outlets or ethernet ports can be exploited by hackers. If a hacker gains physical access to the camera, they can manipulate the settings, tamper with the footage, or even install malware. Securing physical access points is crucial in preventing unauthorized access. Ensure that your cameras are placed in secure locations, and consider using locks or tamper-resistant enclosures to protect them.
It’s important to note that hacking into someone else’s wireless security camera is illegal and unethical. The information provided in this section aims to shed light on the potential risks and vulnerabilities. As a responsible user, it is paramount to prioritize the security of your own devices and take necessary precautions to safeguard them from unauthorized access.
Potential Consequences and Legal Implications
Hacking into a wireless security camera, whether for malicious intent or curiosity, can have serious consequences both legally and ethically. It is important to understand the potential ramifications before engaging in any unauthorized access to someone else’s device. Here are some of the potential consequences and legal implications:
Invasion of Privacy
Unauthorized access to someone’s wireless security camera is a severe invasion of privacy. By gaining access to the camera’s footage, you are violating the individual’s right to privacy and potentially exposing their personal lives to the public or fraudulent activities.
Read more: How To Connect Wireless Security Cameras?
Criminal Offense
Hacking into someone else’s wireless security camera is illegal in most jurisdictions. It is considered unauthorized access to a computer system, which is a criminal offense. Engaging in such activities can lead to criminal charges, fines, and even imprisonment, depending on the laws of the country or state where the act is committed.
Destruction or Manipulation of Property
Unauthorized access to a wireless security camera can enable a hacker to manipulate the camera’s settings, tamper with the footage, or even install malicious software. This can lead to destruction of property, loss of important evidence, or disruption of security systems, leaving the property vulnerable and at risk.
Civil Lawsuits
Individuals or businesses whose wireless security cameras have been hacked may pursue civil legal action against the hacker. This can result in significant financial penalties and legal liabilities for the hacker, including compensatory damages for any harm caused and legal fees incurred by the affected party.
Reputation Damage
Hacking someone’s wireless security camera can have severe reputational consequences. If you are found guilty or suspected of engaging in unauthorized access, your personal or professional reputation may be irreparably damaged. This can impact future employment opportunities, relationships, and overall public perception of your character.
Read more: How Is A Wireless Security Camera Powered
Ethical Considerations
Engaging in any form of hacking, even for educational or research purposes, raises ethical concerns. It is essential to respect the privacy and property of others and to act within the boundaries of the law. Instead of attempting to hack into someone’s wireless security camera, it is advisable to focus on ethical activities such as securing your own devices, educating others about cybersecurity best practices, or pursuing a career in cybersecurity where you can use your knowledge for the betterment of society.
It is crucial to be aware of the potential consequences and legal implications of hacking into wireless security cameras. Protecting personal privacy, respecting the law, and considering the ethical implications of our actions are fundamental in maintaining a safe and secure digital world for everyone.
Protecting Your Wireless Security Camera
Securing your wireless security camera is crucial in ensuring the privacy and protection of your property and loved ones. By implementing a few key measures, you can significantly enhance the security of your devices. Let’s explore some essential steps to protect your wireless security camera:
Changing Default Credentials
One of the simplest yet often overlooked steps is to change the default credentials of your wireless security camera. Many cameras come with pre-configured usernames and passwords, making them an easy target for hackers. By changing these default credentials to unique and strong passwords, you significantly reduce the risk of unauthorized access to your camera.
Strengthening Encryption
Ensure that your wireless security camera uses strong encryption protocols to secure the transmission of data. Look for cameras that support WPA2 encryption, which is currently the most secure encryption standard available. Weak or outdated encryption can make your camera susceptible to hacking attempts. By using strong encryption, you make it significantly more difficult for hackers to intercept or tamper with your camera’s footage and data.
Read more: How To Find Wireless Security Camera?
Regularly Updating Firmware
Firmware updates are crucial for maintaining the security and functionality of your wireless security camera. Manufacturers release regular firmware updates to address security vulnerabilities, improve performance, and introduce new features. Make it a habit to regularly check for firmware updates for your camera and install them promptly. Keeping your camera’s firmware up to date ensures that any known vulnerabilities are addressed, keeping your camera secure.
Securing Physical Access Points
Physical access points to your wireless security camera, such as power outlets or ethernet ports, should be adequately secured to prevent unauthorized access. Place your camera in a location that is not easily accessible to others. Additionally, consider using physical deterrents such as locks or tamper-resistant enclosures to protect your camera from external interference or tampering.
Network Segmentation
If you have multiple wireless security cameras or other IoT devices connected to your network, consider implementing network segmentation. By separating your cameras from other devices on your network, you limit the potential attack surface. This means that even if one device is compromised, it will be more challenging for an attacker to gain access to other devices or sensitive information.
By following these steps, you can significantly enhance the security of your wireless security camera and protect yourself from potential unauthorized access. Remember that maintaining security is an ongoing process, and staying vigilant about updating passwords, firmware, and employing best practices is crucial. By prioritizing the security of your devices, you can have peace of mind knowing that your property is well protected.
Conclusion
Wireless security cameras provide an effective and convenient way to enhance the security of your home or business. However, it’s crucial to be aware of the vulnerabilities and potential risks associated with these devices. By understanding the different types of wireless security cameras, how they work, and the security measures they offer, you can make informed decisions when it comes to protecting your property.
Identifying vulnerabilities in wireless security cameras, such as default credentials, weak encryption, lack of firmware updates, and physical access points, allows you to take proactive steps in securing your devices. Changing default credentials, strengthening encryption protocols, regularly updating firmware, and securing physical access points are essential measures in protecting against unauthorized access and maintaining data privacy.
It’s important to note that hacking into someone else’s wireless security camera is illegal and unethical. The information provided in this article is meant for educational purposes only, to create awareness about the vulnerabilities and best practices for securing wireless security cameras.
By following the recommended steps and best practices outlined in this article, you can significantly enhance the security of your wireless security cameras and protect your property from potential threats. Prioritizing the security of your devices not only ensures the safety of your loved ones and belongings but also helps to create a more secure digital environment for everyone.
Remember, security is an ongoing process. Stay vigilant, regularly update your passwords and firmware, and keep up with the latest trends and advancements in the field of home security and surveillance. By doing so, you can enjoy the peace of mind that comes with knowing your wireless security cameras are well protected.
Frequently Asked Questions about How To Hack Into A Wireless Security Camera
Was this page helpful?
At Storables.com, we guarantee accurate and reliable information. Our content, validated by Expert Board Contributors, is crafted following stringent Editorial Policies. We're committed to providing you with well-researched, expert-backed insights for all your informational needs.